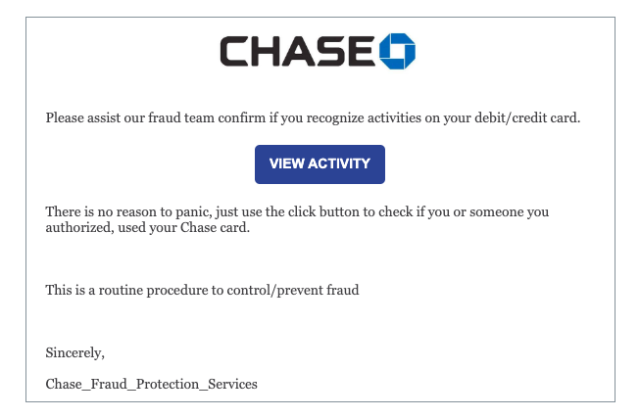
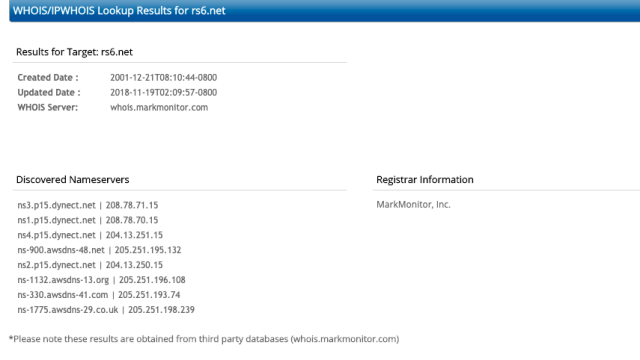
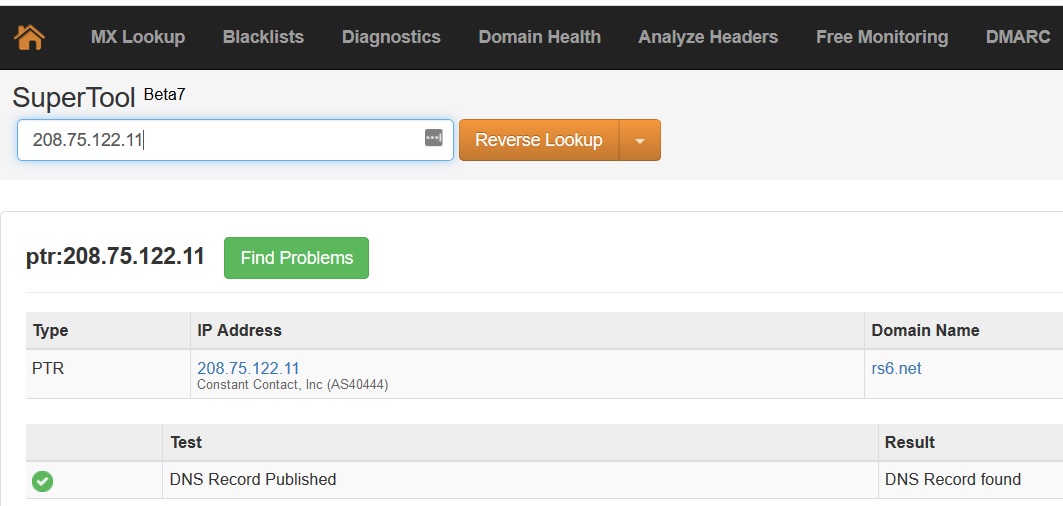
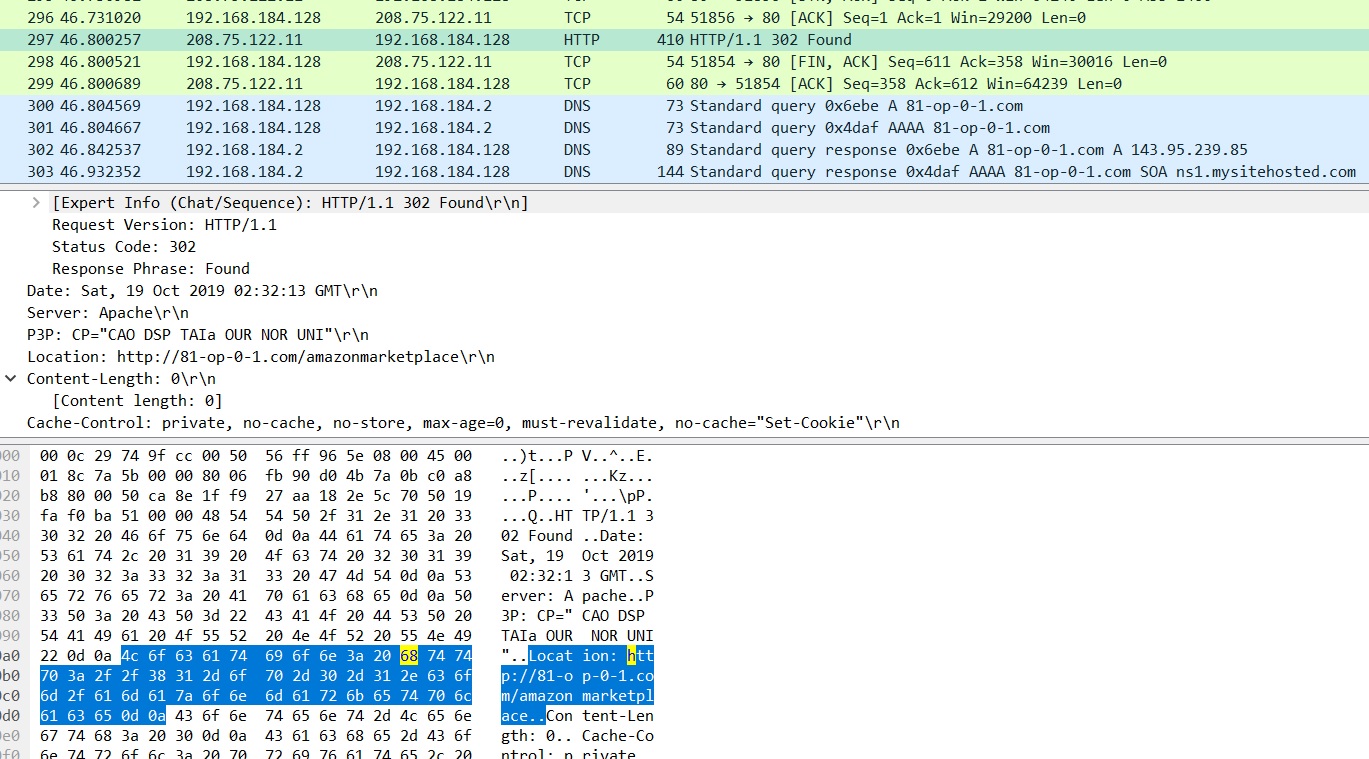
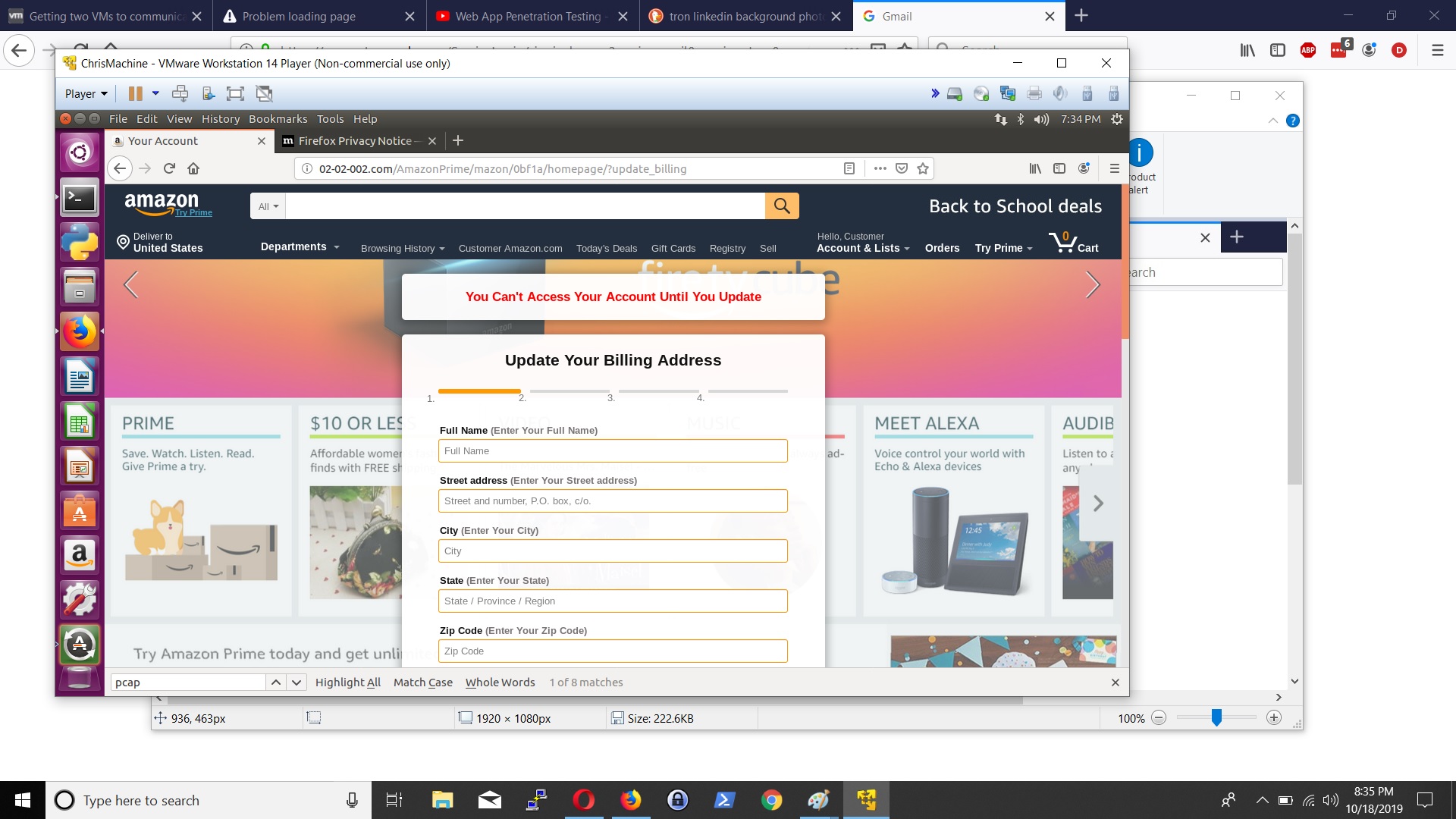
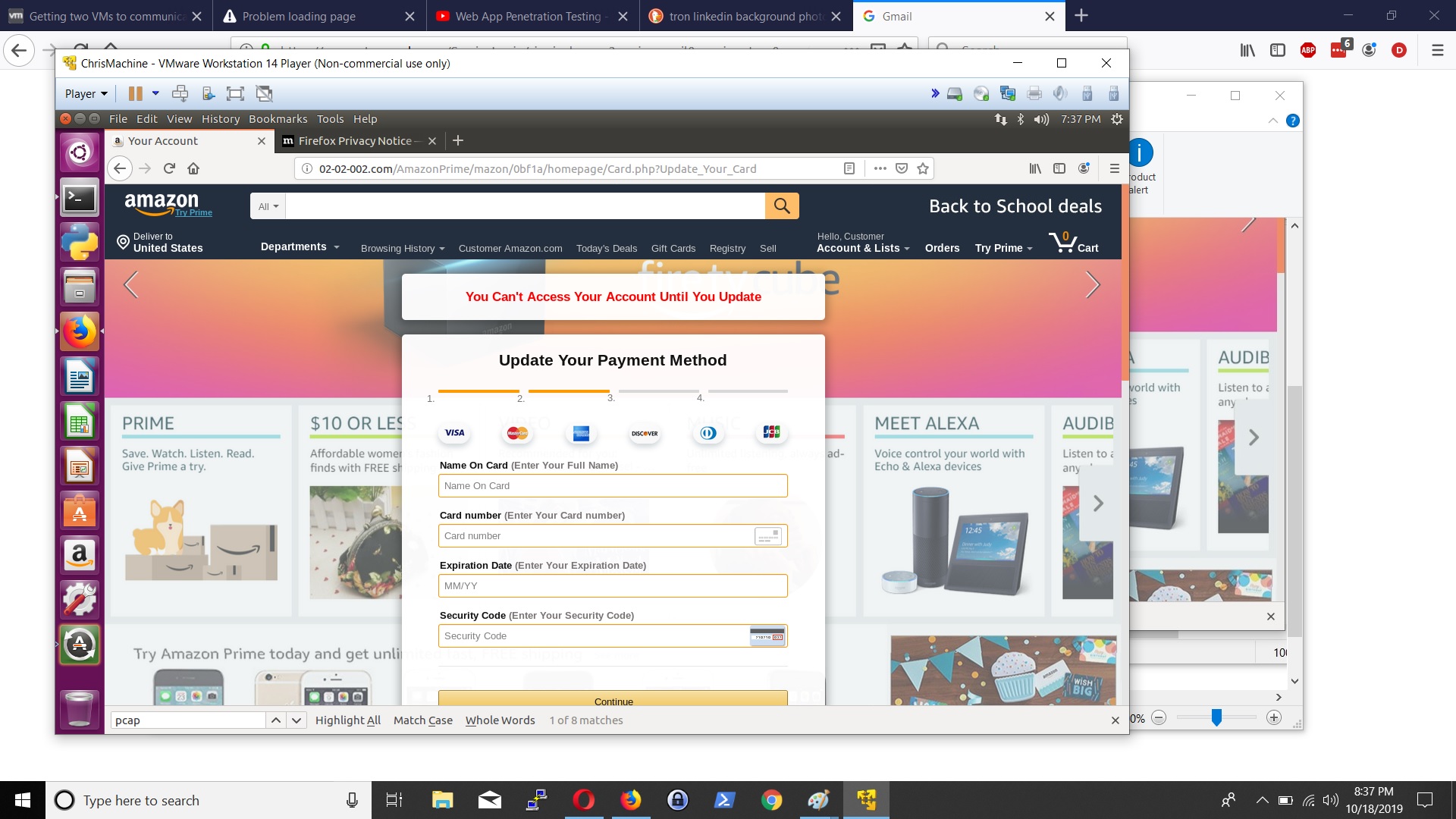
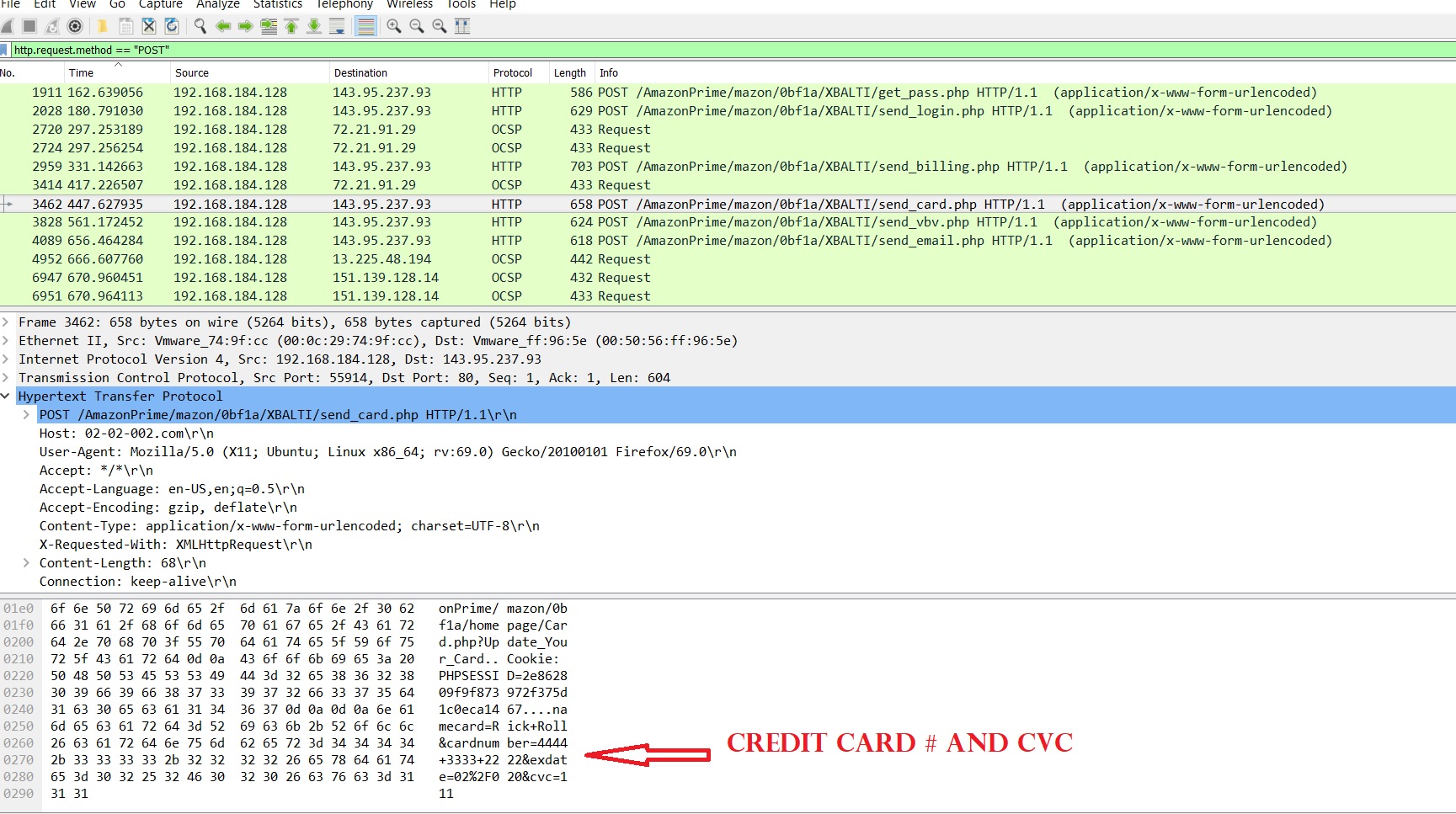
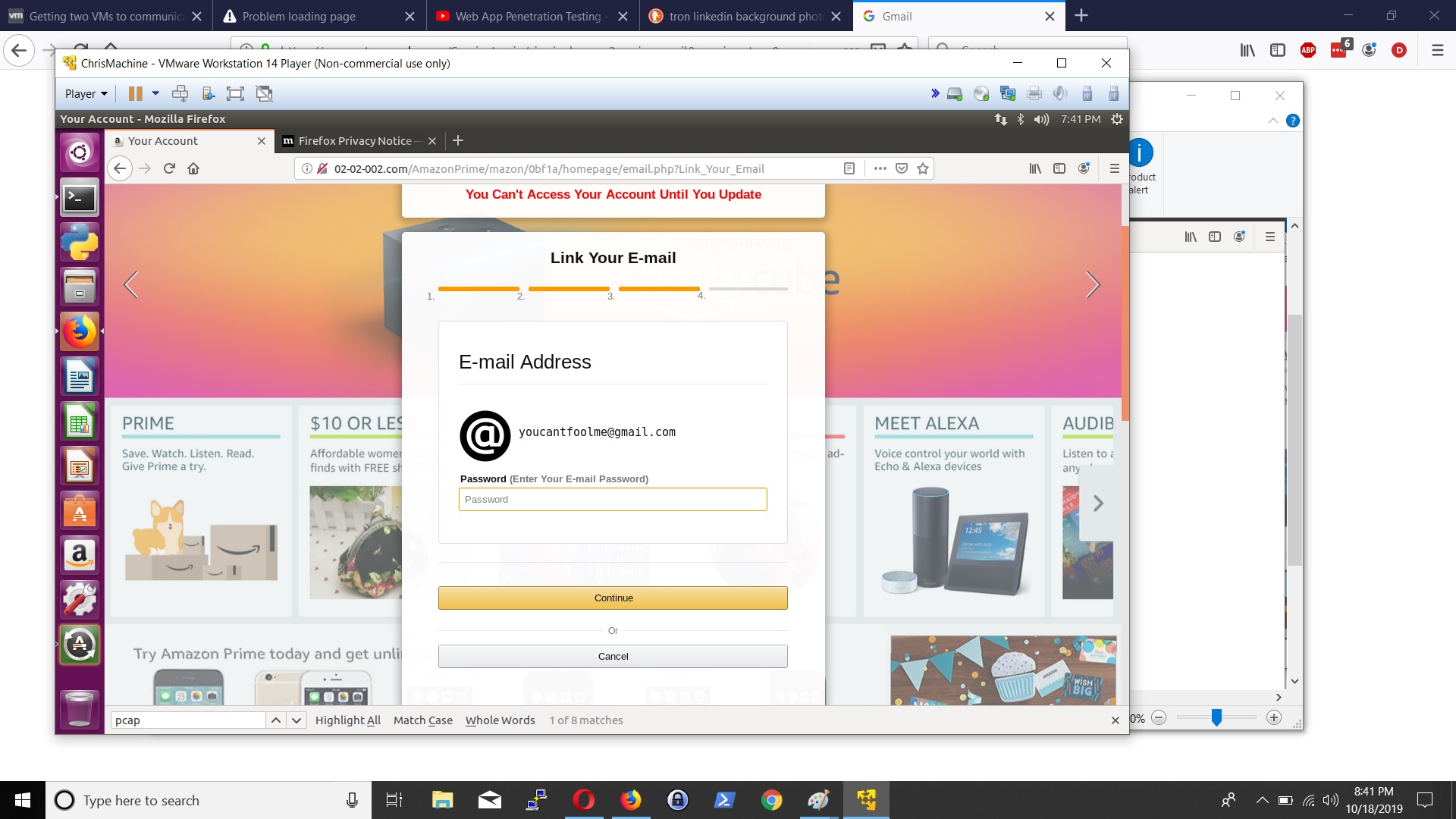
Hi Security nerds. In my learning GCP journey, I came across Google Cloud’s DLP Solution ; and immediately, I think ‘hey that is cool – they have a Data Loss Prevention tool built in to GCP’ and can stop data going out the door.
The truth is a little less satisfying. Although there are some data masking features, (which I’ll get to here in a minute), GCP Cloud DLP is a Data Classification Tool (with some data masking abilities). In Google’s words:
“Cloud DLP gives you the power to scan, discover, classify, and report on data from virtually anywhere. Cloud DLP has built-in support for scanning and classifying sensitive data in Cloud Storage, BigQuery, and Datastore, and a streaming content API to enable support for additional data sources, custom workloads, and applications”
This miffs me a bit because…
Part of the issue here is DLP acronym actually has two meanings. I understand DLP to mean…..Data Loss Prevention as Gartner defines it – and when talking about DLP tools the last ten/fifteen years or so, they typically include the ability to actively block /prevent data from going out the door.
The same acronym has a watered down version, DLP can also mean Data Loss Protection. So, okay, I’ll be fair – Let’s go by Gartner’s definition for Data Loss Protection DLP, which talks a lot about scanning and classifying which Cloud DLP does. However, in the tool page; Google is calling it ‘Cloud Data Loss Prevention’ !
Yeah, Cloud DLP a Data Classification Tool named like a Data Loss Prevention Tool. Ok, so you may say ‘ well wait, google also says Cloud DLP can ” mask, tokenize, and transform sensitive elements “. Yes, those things prevent sensitive data loss; not data loss.
So, what we have here industry buzzword marketing vs. functionality ; and in the mind of this Engineer, the product is inappropriately named because its name infers functionality the product actually does not do. Thinking a tool rename is in order… call it GCP’s Amazing Data Classifier and Masker. Or TaggadyMcDataTagger or.. ?
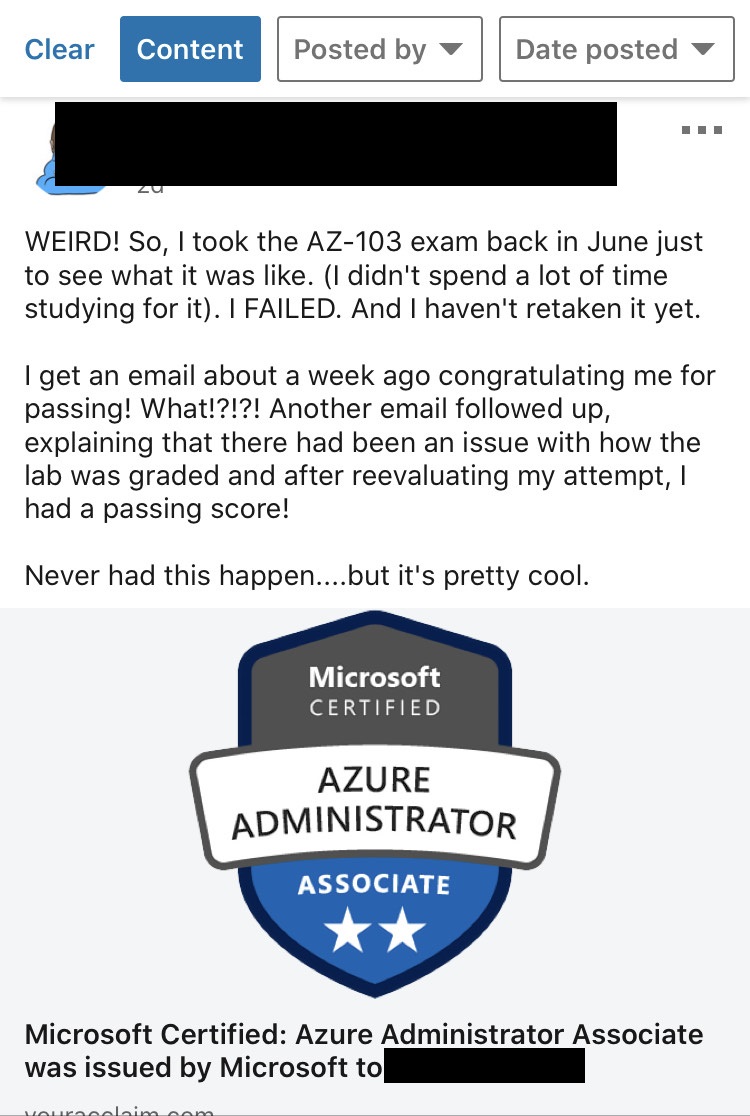
Funny how I came across this; I was doing a practice test for my Google Cloud Security Engineer Professional certification and I came across a question about Cloud DLP, which I got wrong because Google Cloud DLP does not actively stop data exfiltration; it can scan, classify, mask and transform data. Hahaha.